As frequent internet users, we are all the time exposed to different threats lurking online. Not only computers are at risk, but all the devices we tend to carry with us daily. Malicious programs appear in the form of tempting ads, that offer exactly what you need, inviting you to click them. The results can be devastating, due to our ignorance and curiosity.
Ransomware is one of the most common cyber threats that occur daily. They are also potentially some of the most dangerous cyber-attacks and are initiated by individual hackers, professional hackers, and criminal syndicate groups. Their main purpose behind initiating such an attack could be either to cripple your business, to take revenge if it’s a competing firm, or to take control of your intellectual property. Irrespective of whatever may be the motive, the hacker or group could access all your personal files, your customer data, and all your emails.
What is ransomware?

Source:cloudwards.net
The name itself says a lot about the aim of this malware. It’s nothing else than a digital ransom. Someone steals something precious from you and asks for the money, in return. Until you pay or react in another way, you’re held, hostage.
Ransomware is defined as a form of malware that can encrypt a victim’s company or individual’s files. With that leverage in hand, the hacker or attacker likely demands a ransom in order to fix the files in their original form. Ransomware is essentially any malware planted with the sole motive to extort money from the victim, and the ransom is usually demanded in Bitcoin or any other form of cryptocurrency to then relieve the victim of this burden of cybercrime.
How does ransomware work and is applied?
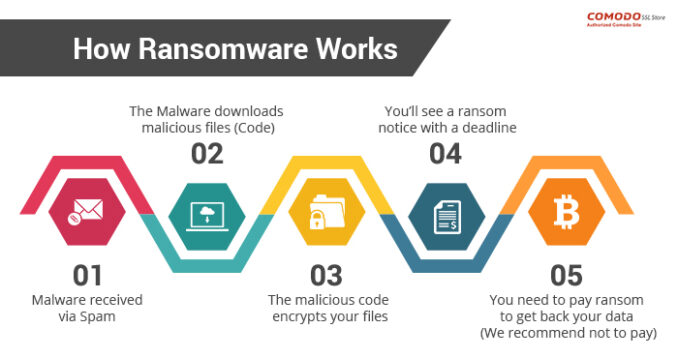
Source:comodosslstore.com
Ransomware is planted through a number of means which typically include phishing or spamming the target individual or company with emails. Such emails typically contain faulty attachments that once downloaded encrypt the user’s files and computer system. These files look like harmless attachments, but actually have dangerous social-engineering tactics embedded into them that can trick a computer into giving them access as the administrator.
Once your files in the computer get encrypted, they can only be decrypted by a certain key, that is set by and known by the hacker or attacker. In very Hollywood style, the attacked and infected computer displays messages directed by the hacker that their computer has been taken over and their files will only be decrypted or recovered by them if they forward a said amount to the hacker.
In case the user or individual doesn’t need to recover any data, the attacker could also threaten them to leak sensitive data into the public if the ransom isn’t paid. This is an alternative form of ransomware and could potentially be very dangerous to the individual’s data and reputation too.
A typical form it uses for the attack is the e-mail. Some of these phishing malwares is installed on certain websites, mostly those with adult content, aiming to analyze your behavior on the internet. Once it figures out your pattern – the website you most frequently use, things you google, ads you like to click on, it sends you a threatening e-mail. Saying it has noticed your inappropriate activity during working hours, and threats to reveal it publicly if you don’t perform a transaction of a certain amount of money in a given time.
Once you become a victim of such a virus, it can potentially spread to other equipment, via a server network. So, it’s important to take it seriously and react by noticing others.
Who is a typical target for ransomware attacks?

Source:kaspersky.com
Hackers may choose their target for ransomware for several reasons. The reasons may range from ease of access to the probability of sensitive data and payment, etc. Hackers are likely to attack companies or organizations which have smaller IT teams and a big user database that relied on file sharing such as a school or university.
Some companies or organizations simply don’t think they will ever be victims of such an attack, which is not the case. This kind of attitude is exactly what the hackers search for. For huge organizations, it would take a lot of investment to upgrade their security system, which is why they tend to delay it. Smaller ones, on the other hand, have a limited budget and therefore don’t invest in systems. It’s just not their priority. Even when they do choose to upgrade the security system, they either have the troubles of installing and maintaining or compatibility with the current operating system they use.
Similarly, hackers can also choose an organization to attack purely because they may have more sensitive information and hence pay whatever ransom they ask for.
How can one prevent ransomware attacks?
There are a number of steps that a company can undertake to prevent ransomware attacks which include the following:
- By regularly updating your operating system you can make sure that your systems are fortified against any such potential attacks
- By not installing any software that requires administrative privilege until and unless you are absolutely sure about the developer and the software and they both are reputed.
- By installing antivirus and antimalware software you can ensure that you give your computer system a significant amount of protection against ransomware.
- By regularly backing up your files you can ensure that in case of a ransomware attack you have access to your files and data. Have a safety copy, such as an external disk drive or server at your disposal, and don’t keep it connected to the computer, because it can also be affected by the ransomware.
- By not storing any sensitive personal data on their professional computers.
- By not opening different commercials that pop-up or stand on portals. Therefore, installing some kind of add-on to the browser that prevents malicious ads from showing is advisable.
- By creating a restore point on your system.

Source:csoonline.com
If, however, you do find yourself a victim of such an attack, there are some services specialized in cyber-attacks that can help you with regaining what is yours, such as cytelligence.com. They act the same as police would after you seek their help and report the case to them. They have the tools and knowledge to open an investigation, and with a little bit of luck find out who might be behind the attack.
Being a victim of ransomware can be a very traumatizing experience that may make you suffer a lot. Hence it is necessary to make sure that you take all the preventive measures you can.